I have used X-Ways and Winhex ever since I started my digital forensics career in 2012, thanks to IACIS, whose BCFE training course uses Winhex to train students to navigate through file systems and file data.
These tips are for those who are either new to forensics or haven't used X-Ways and have some interest in using it. Also, here are some handy resources to help when researching X-Ways:
- http://www.x-ways.net/winhex/manual.pdf
- http://www.x-ways.net/forensics/XWFQuickStart.pdf
- https://www.amazon.com/X-Ways-Forensics-Practitioners-Guide-Shavers/dp/0124116051
1 - Create a case and set case options
When you are about start analysis on a new piece of evidence, you should almost always create a case within X-Ways. You have several options to set when create a case:
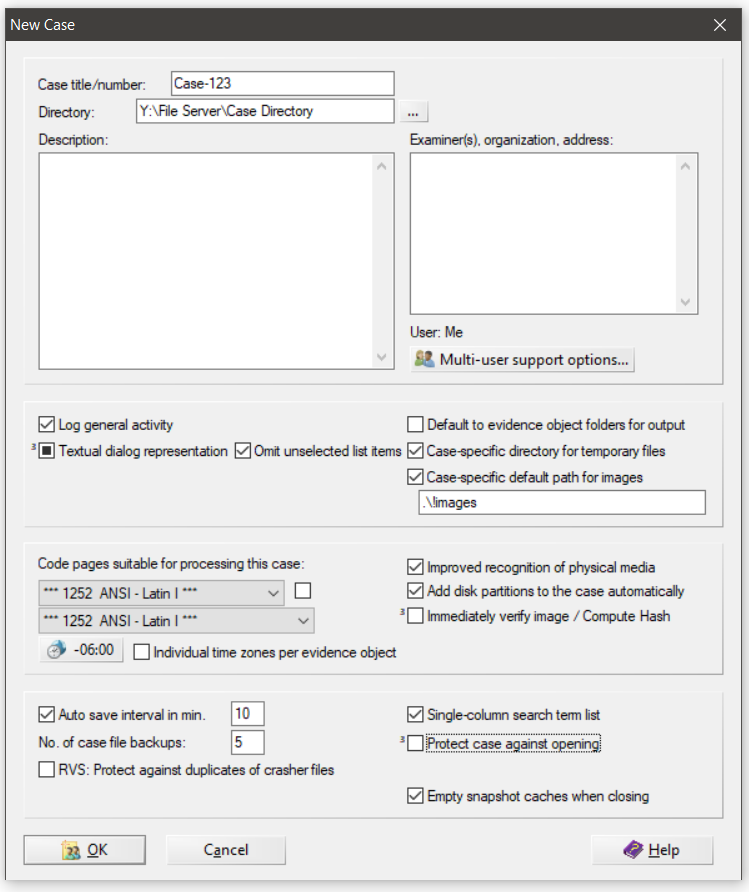
Here is a list of the options I pay attention to the most when I create a new case:
Case Title/number -
- This will effectively "Name" the X-Ways case so that you can easily find it and know what it is by reference. X-Ways will create a case folder with a lot of cache files and system files related to this case. Its good practice to keep these cases separate with appropriate names for easy management.
Directory -
- This is where X-Ways is going to place all if its cache, temp, and db files. These are required for an X-Ways case to operate efficiently. Consider setting this to a fast SSD to get quick load times when using X-Ways, but I have had good results with placing the case directory on standard NAS and file shares.
Case-specific directory for temporary files -
- This is a good house cleaning measure - anytime X-Ways creates temporary files, they will be stored in a temp directory related to the case rather than your default temp location.
Case-specific default path for images -
- Set this to the location of all your forensic images in a case. This will make your life a lot easier when you want to add new images as your work progresses. You wont have to drill through you file system every time to add a new evidence item.
Timezone -
- Make sure to set your timezone appropriately as it may default to your system's settings. I usually set it to UTC and then change it during analysis if I want to.
Once these settings are set, click "OK" to create the case and start your analysis.
2 - Load an $MFT File for Analysis -
One of my favorite features of X-Ways is its ability to load an extracted MFT file like a forensic image. There are tons of tools out there to handle MFT analysis, but X-Ways produces a view of the MFT like you are navigating a full file system.
There are two ways to load an MFT into X-Ways; with a case and without a case:
Load an MFT with an X-Ways case:
- In the Case Data window within X-Ways, select File->Add Image
- This will open a Windows file browser window.
- Navigate to the exported MFT file you want to analyze, select it, and click Open.
- X-Ways will add the MFT file to you evidence list and being parsing it immediately, given that you have the "Add disk partitions to the case automatically" option set in your case preferences.
- If that option isnt set, just double-click the MFT once it is added to your evidence list and X-Ways will being parsing.
3 - File System Recursion -
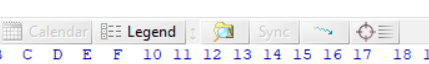
This is a feature I use all the time during analysis. When you have evidence loaded into X-Ways and are browsing the file system, there is a squiggly blue arrow button in the bottom toolbar. This is the Explore Recursive option.
By clicking this button, X-Ways will completely flatten the file system into one level and let you see every single file and folder on one view.
In the Directory Browser options you can select whether Directories are shown and whether they should be grouped together or mixed with files.
This is a very handy function to have when tracing activity on a system, especially ransomware or general malware analysis. From the recursive view you can quickly sort by any of the primary timestamps and layer two additional sorts. This can quickly reveal additional files and directories related to the incident you are investigating.